Put yourself in the patient's shoes for a minute.
A trip to urgent care for a sprained ankle may seem like an inconvenience, but it’s also a treasure trove of information. In addition to taking x-rays, the staff members are asking you what medications you're on, where you were when you injured yourself, and all sorts of personal information.
Their system may also be linked to a health-care entity that shares data about your entire medical history and personal information like your emergency contacts, social security number, family health history and even your mother’s maiden name. When it's all said and done, then you have to pay or make a co-pay.
That's a lot of information to share. In the age of high-stakes data breaches and treasure troves of information being compromised -- as a patient -- it can be unnerving.
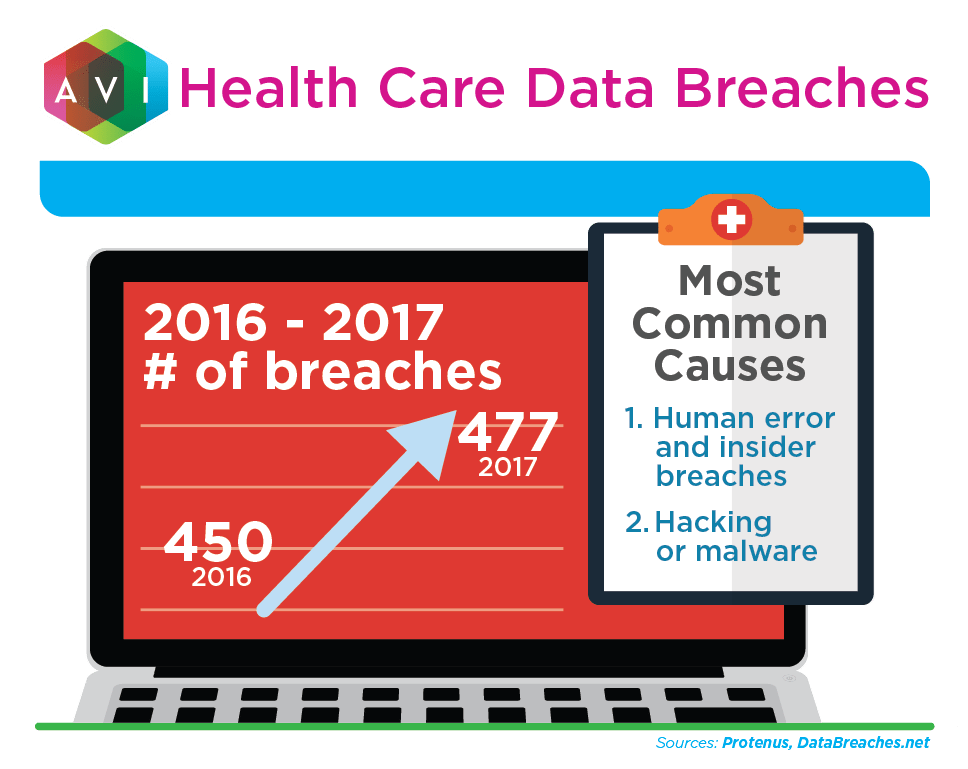
All the personal, medical, and financial information collected by health-care facilities can be a tempting target for hackers. But the bigger threat is often insider mistakes and wrongdoing.
Whatever the cause of a breach, you don’t want data getting into the wrong hands. You don’t want your facility or organization to be the weak link that allowed a data breach to happen.
Unfortunately, many health-care organizations will find themselves in the news for just that reason. More than 40 percent of breached records come from the health-care industry.
Data Management and Security
Health-care data is among the most personal and legally protected data that organizations must worry about. And the sheer volume of it makes it especially challenging to manage.
The breach of personal, medical, and financial information can have serious consequences for both the patient and the facility.
Health-care facilities generate a lot of data: radiology images, lab tests, computer files, video consultations, recordings of surgeries, and more.
The data has to be processed, stored, organized, retrieved when needed, and sometimes transmitted to other facilities. Now, it's often shared with patients through online portals.
That means data must be protected where it is generated, where it is stored, and where it is transmitted and shared. Weak points include the equipment itself, cloud storage, internal and external networks, and especially the people managing the data. Health-care workers must be trained and vetted to secure data and to use technologies correctly.
[Read how one school uses technology to train medical students.]
Firewalls and data encryption are some of the ways to protect patient data, but another major consideration in managing data securely and efficiently is whether your organization employs and partners with professionals who understand health-care data laws, technologies, and risks.
Data Storage and Compliance
Fines, penalties, and lawsuits are some of the consequences of non-compliance with patient data security laws and protections like HIPAA, the Health Insurance Portability and Accountability Act. Loss of trust can also have long-term effects on your organization.
The risks of data storage are real, and many state laws require doctors and hospitals to retain patient records for long periods of time.
Organizations must, therefore, consider short-term options, long-term options, disaster recovery methods, what kinds of data they will keep on-premises, what they will keep in the cloud, and more.
Some organizations are looking into storage solutions like flash storage or blockchain, but it’s important to make sure the solution is industry-compliant and deployed with security considerations in mind.
What’s Next
Data security isn’t all about the technologies or even the people working with the data. Effectively securing your organization’s data starts with a well-thought-out plan.
It also means conducting frequent risk assessments and staying up to date on regulations and the latest tactics by cyber thieves.
Technology is constantly evolving and so are the threats. Your greatest countermeasure is to be proactive and remain vigilant. Stay up to date and seek expert advice from technology specialists when in doubt.
Share your questions or comments about data security with us on social media. Or, feel free to contact us to learn more about health-care technologies.







